Content
There is an overview of the SPAM Blocking process here.
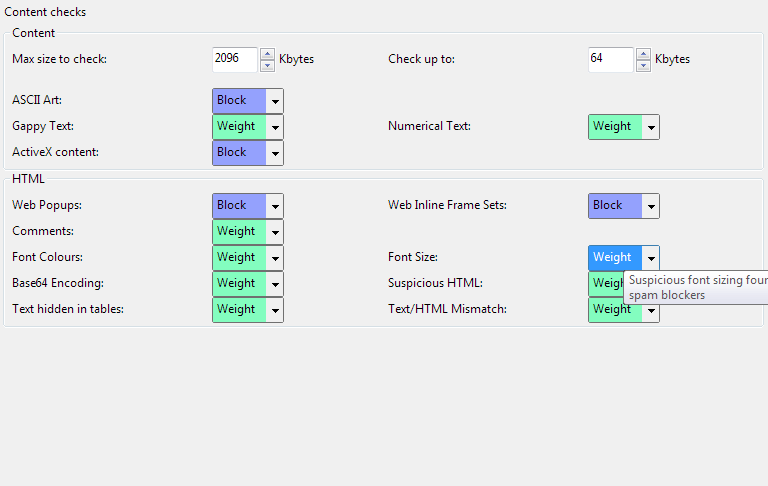
Content
Max size to check
The spam blocker will only spam check email less than this size. The size includes any attachments. Typically spam email are relatively small due to the volume spammers must send. It is more efficient to avoid processing the larger email as they are often not spam and take longest to check.

2 - 256000 Kbytes
2096 Kbytes
Check up to
The spam blocker will only check up this amount of an email to work out if it is spam or not. Often only the first few parts of the email (the text and html parts) need be checked, so this setting can save processing the rest of the message. Typically you will not want to set this much higher than the default of 64kbytes

1 - 256000 Kbytes
64 Kbytes
Gappy Text
G-a-p-p-y text found in the email, this form of text is often used by spammers to foil spam blockers. As this practice is used to circumvent blocking: it is a highly reliable mechanism for detecting spam
Numerical Text
Numerical text (e.g Sc00l, 1esb1ans, y0ung, g1rls) found in the email, this form of text is often used by spammers to foil spam blockers. As this practice is used to circumvent blocking: it is a highly reliable mechanism for detecting spam
HTML
Web Popups
This rule identifies email where a pop-up windows are opened by the email on receipt. This is often a trick by SPAMmers to force users to view webpages (even the preview pane of an email client will pop open the window). Usually confined to SPAM email, but annoying in every case - so well worth blocking!
Web Inline Frame Sets
This rule identifies email where a an embedded frameset is used to show HTML content in the email without the email containing the content itself. This is often used to allow spam to deliver is content undetected. It is almost never used today in legitimate email
Comments
Suspicious comments found in the email, often used by spammers to foil spam blockers. As this practice is used to circumvent blocking: it is a highly reliable mechanism for detecting spam
Font Colours
Suspicious font coloring found in the email, often used by spammers to foil spam blockers. As this practice is used to circumvent blocking: it is a reliable mechanism for detecting spam
Font Size
Suspicious font sizing found in the email, often used by spammers to foil spam blockers.
As this practice is used to circumvent blocking: it is a highly reliable mechanism for detecting spam
Base64 Encoding
spam is often encoded into Base64 to hide readable content from filters. Content is always decoded before analysis but you can also use the fact it was encoded to block or weight the email